CentOS7.7下源码安装3.0.3版本ModSecurity及配置策略
服务器操作系统:CentOS7.7 64位 需要安装依赖环境如下:
1.需要用到的软件包,推荐丢到/usr/local目录下
下载链接:http://www.modsecurity.cn/practice/files/apache+modsecurity.rar
2.安装依赖工具
yum install -y epel-release
yum install -y readline-devel curl-devel gcc gcc-c++ python-devel lua-devel doxygen perl yajl-devel GeoIP-devel lmdb-devel ssdeep-devel flex bison autoconf automake
3.创建需要的目录
cd /usr/local
mkdir apr apr-util pcre apache libxml2
4.安装apr
在ModSecurity 2版本中安装lua发现暂时没有被使用,可以先不安装
cd /usr/local
tar -zxvf apr-1.5.2.tar.gz
cd apr-1.5.2
./configure –prefix=/usr/local/apr
#结尾会提示rm: cannot remove 'libtoolT': No such file or directory,无需处理
make
make install
5.安装apr-util
cd /usr/local
tar -zxvf apr-util-1.5.4.tar.gz
cd apr-util-1.5.4
./configure –prefix=/usr/local/apr-util -with-apr=/usr/local/apr/bin/apr-1-config
make
make install
6.安装pcre
cd /usr/local
tar -zxvf pcre-8.43.tar.gz
cd pcre-8.43
./configure –prefix=/usr/local/pcre
make
make install
#中间会出现两次警告,不影响最终效果,因此暂不处理
7.安装libxml2
cd /usr/local
tar -zxvf libxml2-2.9.9.tar.gz
cd libxml2-2.9.9
./configure –prefix=/usr/local/libxml2
make
make install
#中间会出现一次警告,libtool: warning: relinking 'libxml2mod.la',不影响最终效果,因此暂不处理
8.安装Apache
cd /usr/local
tar -zxvf httpd-2.4.41.tar.gz
cd httpd-2.4.41
./configure –prefix=/usr/local/apache –with-apr=/usr/local/apr –with-apr-util=/usr/local/apr-util/ –with-pcre=/usr/local/pcre
make
make install
上述安装完成之后修改httpd.conf配置文件,将"#ServerName www.example.com:80"改为"ServerName localhost:80"后启动Apache,这里可以根据实际情况更改
vim /usr/local/apache/conf/httpd.conf
然后启动apahce
/usr/local/apache/bin/apachectl start
9.测试效果
默认没有安装Mod_Security访问是显示It Works
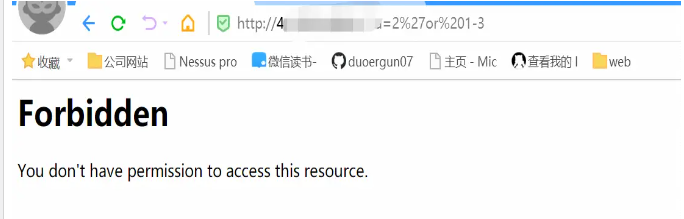
测试语句:http://139.29.13.228/?id=2%27or%201-3
10.安装Mod_Security
#停止Apache
/usr/local/apache/bin/apachectl stop
cd /usr/local
tar -zxvf modsecurity-v3.0.3.tar.gz
cd modsecurity-v3.0.3
./configure
make
make install
11.安装ModSecurity-apache connector
cd /usr/local
tar -zxvf ModSecurity-apache.tar.gz
cd ModSecurity-apache
./autogen.sh
./configure –with-libmodsecurity=/usr/local/modsecurity/
make
make install
12.最终配置
创建用于存放规则文件的文件夹,可以只创建到rules这一层,个人是由于其他自定义规则文件存在,所以默认规则额外创建了一个base文件夹,可以根据个人喜好进行随意配置增加目录或者更改为其他名称
mkdir -p /usr/local/apache/conf/modsecurity/rules/base
复制ModSecurity配置文件
cp /usr/local/modsecurity-v3.0.3/modsecurity.conf-recommended /usr/local/apache/conf/modsecurity/modsecurity.conf
将owasp-modsecurity-crs解压后中的crs-setup.conf.example复制到/usr/local/apache/conf/modsecurity/下并重命名为crs-setup.conf
将owasp-modsecurity-crs解压后rules文件夹内的所有文件复制到/usr/local/apache/conf/modsecurity/rules/base下,同时修改REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf.example与RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf.example两个文件的文件名,将".example"删除,可将自己写的规则放置于此两个文件中,这里就是可以自定义规则
编辑httpd.conf,去掉#LoadModule unique_id_module modules/mod_unique_id.so前的注释符,并添加以下内容:
vim /usr/local/apache/conf/httpd.conf 第113行那里
LoadModule security3_module modules/mod_security3.so
<IfModule security3_module>
modsecurity on
#modsecurity_rules_file指令目前无法匹配通配符,因此只能一个指令引用一个文件
modsecurity_rules_file /usr/local/apache/conf/modsecurity/modsecurity.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/crs-setup.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-900-EXCLUSION-RULES-BEFORE-CRS.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-901-INITIALIZATION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-903.9001-DRUPAL-EXCLUSION-RULES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-903.9002-WORDPRESS-EXCLUSION-RULES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-903.9003-NEXTCLOUD-EXCLUSION-RULES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-903.9004-DOKUWIKI-EXCLUSION-RULES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-903.9005-CPANEL-EXCLUSION-RULES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-903.9006-XENFORO-EXCLUSION-RULES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-905-COMMON-EXCEPTIONS.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-910-IP-REPUTATION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-911-METHOD-ENFORCEMENT.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-912-DOS-PROTECTION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-913-SCANNER-DETECTION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-920-PROTOCOL-ENFORCEMENT.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-921-PROTOCOL-ATTACK.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-930-APPLICATION-ATTACK-LFI.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-931-APPLICATION-ATTACK-RFI.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-932-APPLICATION-ATTACK-RCE.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-933-APPLICATION-ATTACK-PHP.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-934-APPLICATION-ATTACK-NODEJS.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-941-APPLICATION-ATTACK-XSS.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-942-APPLICATION-ATTACK-SQLI.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-943-APPLICATION-ATTACK-SESSION-FIXATION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-944-APPLICATION-ATTACK-JAVA.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/REQUEST-949-BLOCKING-EVALUATION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-950-DATA-LEAKAGES.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-951-DATA-LEAKAGES-SQL.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-952-DATA-LEAKAGES-JAVA.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-953-DATA-LEAKAGES-PHP.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-954-DATA-LEAKAGES-IIS.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-959-BLOCKING-EVALUATION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-980-CORRELATION.conf
modsecurity_rules_file /usr/local/apache/conf/modsecurity/rules/base/RESPONSE-999-EXCLUSION-RULES-AFTER-CRS.conf
</IfModule>
开始编辑modsecurity.conf
vim modsecurity.conf
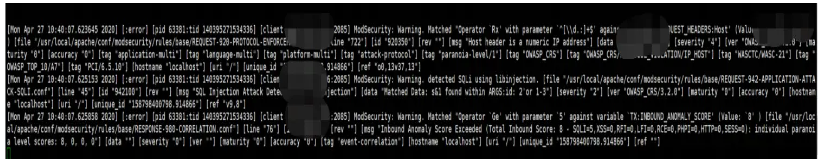
SecRuleEngine DetectionOnly改为SecRuleEngine On,将SecUnicodeMapFile unicode.mapping 20127注释;
13.启动Apache
上面测试过程已经启动了Apache,可以先停止再启动
/usr/local/apache/bin/apachectl stop
/usr/local/apache/bin/apachectl start
测试访问: http://42.1xx.142.81/?id=2%27or%201-3
转自:https://www.jianshu.com/p/ea3e87a94b27
